DCDIAG – диагностика здоровья AD одной утилитой
Авторское примечание: Статья в первую очередь написана для начинающих системных администраторов, опытные вряд ли почерпнут для себя здесь что-нибудь новое и полезное. Навеяно статьей про GPUPDATE /force (спасибо mrHobbY).
Active Directory – это большой и сложный организм (даже если он состоит и двух контроллеров домена и одного сайта), и для системного администратора очень важно в любой момент времени провести диагностику для анализа работы этого организма.
Ну, а так как по оснасткам ходить и смотреть малоэффективно, по логам системы тоже не всегда поймешь, что происходит, поэтому на помощь приходят различные утилиты. Одна из них – dcdiag от компании Microsoft.
Посмотрим на нее внимательно – ибо полезность данной утилиты трудно переоценить. Я не буду приводить многочисленные ключи данной команды – про них при желании можно и в справке прочитать — а остановлюсь только на тех, – которые использую сам при диагностике на практике.
Первое, что нужно сделать, чтобы работать с этой утилитой – это установить ее к себе на рабочую станцию или на сам сервер (тут каждый волен выбирать сам, но в последних версиях dcdiag – уже в помощи написано, что проверки необходимо запускать на самих серверах — контроллерах домена, за исключением тестов dcPromo и RegisterInDNS). Для Windows 2003 необходимо установить пакет Support Tools c дистрибутива операционной системы, для Windows 7 и 8 – необходимо установить пакет Remote System Administration Tools (они разные для win7, win7sp1, и win8 – будьте внимательны, когда будете скачивать). Кстати, RSAT — сам по себе полезный продукт – внутри много утилит, которые просто необходимы в повседневной жизни администратора домена.
После установки пакета команда уже доступна из командной строки.
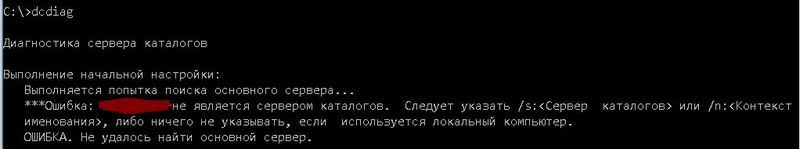
Но не торопитесь запускать ее сразу, на рабочей станции ничего не получится без указания контроллера домена, к которому надо подключиться. Утилита выдаст соответствующее предупреждение:
Примечание: начиная с Windows 7 сообщения dcdiag переведены на русский. До этого – все только на английском. Может будет кому полезно. Хотя и в старых версиях очень простой и понятный английский язык.
Замечательно – мы выяснили – что желательно указать контроллер домена с помощью ключа /s: или контекст именования – /n:. Какой сервер указывать понятно – тот контроллер домена, который вы хотите проверить – а вот если указать контекст именования домена – (имя домена другими словами – можно указывать в форматах Netbios, DNS или DN.), то будет найден ближайший (в пределах сайта) контроллер домена (далее КД).
Проведем самую простую проверку: dcdiag /s:dc01-local
И опять беда, хотя кое-что уже видно:
Как мы видим, часть тестов пройдена – но части отказано в доступе. Это из-за того, что dcdiag я запускал из-под обычной учетной записи домена, без администраторских прав. Понятно – что часть проверок пройти под ней просто невозможно. Поэтому, что бы получить правильную диагностику, необходимо запускать утилиту с административными полномочиями – либо запустить командную строку от имени администратора, либо использовать ключи /u: имя домена\имя пользователя и /p: пароль. Попробуем:
dcdiag /s:dc01-local /u:local\user19 /p:Password
ак видим, проверки пройдены почти все – кроме проверки Services. Но тут у меня есть вполне логичное объяснение – я с помощью новой утилиты (из пакета для windows 7) пытаюсь проверять контроллер домена на базе win2003 – и вполне возможно, название службы может отличаться.
Лирическое отступление №1. При подготовке статьи я столкнулся с epic fail забавным феноменом, может в комментариях обсудим? :). В общем, запуская dcdiag из-под обычной учетной записи другого домена (связанного доверительными отношениями с исследуемым доменом local) и задавая параметры /u и /p – (имя пользователя и пароль административной учетной записи домена local) – утилита выдавала ошибки в части проверок — например sysvolchek (в версии dcdiag 2003 – frssysvol). Если же на рабочую станцию зайти под учетной записью с административными полномочиями в домене local — проверки прекрасно проходятся. Так что – может быть, все-таки не лишним будет проводить проверку на самом сервере. Конец лирического отступления №1.
Полностью описывать результаты работы команды я не вижу смысла. Это прекрасно описано в помощи к утилите (dcdiag /h). Видно главное – с данным контроллером домена проблем нет и все тесты пройдены. Но из проверки одного сервера – не следует факт, что AD сейчас находится в шоколаде работоспособном состоянии. И вот здесь нам на помощь придет ключ для проверки всех серверов предприятия.
Это ключ /e. Данный ключ заставляет утилиту обойти все КД в домене с запуском всех тестов на каждом сервере. Полезно вместе с этим применить /v – вывод расширенной информации по каждому тесту. Ну и чтобы проанализировать все это – полезно данные вывести в файл – причем лог отдельно, сообщения об ошибках – отдельно. Помогут в этом ключи /f: имя_файла_лога и ferr:/имя_файла_лога_ошибок (в новых версиях ключ /ferr убран). Если вы хотите провести проверку не того домена, в котором находитесь сейчас – добавите ключ для указания наименования контекста /n:.
Полностью команда выглядит так:
dcdiag /n:local /e /v /f:c:\logs\adtest.log /ferr:c:\logs\aderrors.log /u:local\user19 /p:Password
Внимание! В версиях dcdiag, начиная с windows 2008 ключ /ferr: убран из поддерживаемых (специально повторился :)).
Если у вас сложная структура леса, да еще и с медленными каналами связи приготовьтесь подождать. Да даже и если несложная – скажем у меня в одном реальном лесе – 10 КД, 5 сайтов и каналы 256 кбит/сек. Выполнение данной команды занимает в среднем до 20 минут.
Результат исполнения очень рекомендуется внимательно просмотреть на наличие проблем. Ну и очень желательно запускать данную утилиту регулярно для диагностики здоровья AD.
Для хардкора можно еще добавить ключ /fix – внесение безопасных исправлений, но бездумно все-таки этого делать не стоит.
Вот собственно и все что я хотел сегодня рассказать. А как часто вам приходится пользоваться данной утилитой на производстве? Какие альтернативы вы знаете?
Dcdiag
Applies To: Windows Server 2003, Windows Server 2008, Windows Server 2003 R2, Windows Server 2012, Windows Server 2003 with SP1, Windows 8
Analyzes the state of domain controllers in a forest or enterprise and reports any problems to help in troubleshooting.
As an end-user reporting program, dcdiag is a command-line tool that encapsulates detailed knowledge of how to identify abnormal behavior in the system. Dcdiag displays command output at the command prompt.
Dcdiag consists of a framework for executing tests and a series of tests to verify different functional areas of the system. This framework selects which domain controllers are tested according to scope directives from the user, such as enterprise, site, or single server.
Dcdiag is built into Windows ServerВ 2008В R2 and Windows ServerВ 2008. It is available if you have the ActiveВ Directory Domain Services (ADВ DS) or ActiveВ Directory Lightweight Directory Services (ADВ LDS) server role installed. It is also available if you install the ActiveВ Directory Domain Services Tools that are part of the Remote Server Administration Tools (RSAT). For more information, see How to Administer Microsoft Windows Client and Server Computers Locally and Remotely (https://go.microsoft.com/fwlink/?LinkID=177813).
If Dcdiag takes a long time to run on a computer that runs Windows ServerВ 2008В R2 or WindowsВ 7, install the hotfix in article 979294 (https://go.microsoft.com/fwlink/?LinkId=196596) in the Microsoft Knowledge Base.
To use dcdiag, you must run the dcdiag command from an elevated command prompt. To open an elevated command prompt, click Start, right-click Command Prompt, and then click Run as administrator.
For examples of how to use this command, see Examples.
Syntax
Parameters
Specifies the name of the server to run the command against. If this parameter is not specified, the tests are run against the local domain controller. This parameter is ignored for DcPromo and RegisterInDns tests, which can be run locally only.
Uses NamingContext as the naming context to test. You can specify domains in NetBIOS, Domain Name System (DNS), or distinguished name format.
Uses Domain\UserName. Dcdiag uses the current credentials of the user (or process) that is logged on. If alternate credentials are needed, use the following options to provide those credentials for binding with Password as the password:
Use quotation marks («») for an empty or null password.
Use the wildcard character (*) to prompt for the password.
Tests all the servers on this site.
Tests all the servers in the enterprise. Overrides /a.
Quiet. Prints only error messages.
Verbose. Prints extended information.
Ignores superfluous error messages.
Affects the MachineAccount test only. This parameter causes the test to fix the Service Principal Names (SPNs) on the Machine Account object of the domain controller.
Redirects all output to a log file (LogFile).
Comprehensive. Runs all tests except DCPromo and RegisterInDNS, including non-default tests. Optionally, you can use this parameter with the /skip parameter to skip specified tests.
The following tests are not run by default:
Displays help at the command prompt.
Runs this test only. The Connectivity test, which you cannot skip, is also run. You should not have this parameter in the same command with the /skip parameter.
Tests the connection between the domain controller on which you run the command and the source domain controller. (This parameter is used for the CheckSecurityError test.) SourceDomainController is the DNS name, NetBIOS name, or distinguished name of a real or potential server that will be the source domain controller for replication, as represented by a real or potential connection object.
DNS Test Syntax
The Dcdiag DNS test uses the following syntax:
DNS Test Parameters
/test:DNS [DNS test] Performs the specified DNS test. If no test is specified, defaults to /DnsAll.
/DnsBasic Performs basic DNS tests, including network connectivity, DNS client configuration, service availability, and zone existence.
/DnsForwarders Performs the /DnsBasic tests, and also checks the configuration of forwarders.
/DnsDelegation Performs the /DnsBasic tests, and also checks for proper delegations.
/DnsDynamicUpdate Performs /DnsBasic tests, and also determines if dynamic update is enabled in the ActiveВ Directory zone.
/DnsRecordRegistration Performs the /DnsBasic tests, and also checks if the address (A), canonical name (CNAME) and well-known service (SRV) resource records are registered. In addition, creates an inventory report based on the test results.
/DnsResolveExtNameВ **[/DnsInternetName: ] Performs the /DnsBasic tests, and also attempts to resolve InternetName. If /DnsInternetName is not specified, attempts to resolve the name www.microsoft.com. If /DnsInternetName is specified, attempts to resolve the Internet name supplied by the user.
/DnsAll Performs all tests, except for the /DnsResolveExtName test, and generates a report.
**/f: Redirects all output to LogFile.
**/s: Runs the tests against DomainController. If this parameter is not specified, the tests are run against the local domain controller.
/e Runs all tests specified by /test:DNS against all domain controllers in the ActiveВ Directory forest.
Run times for DNS tests can be significant in large enterprises when the /e parameter is used. Domain controllers and DNS servers that are offline will increase run time as a result of long-time out periods for RPC and other protocols.
/v Verbose. Presents extended information about successful test results, in addition to information about errors and warnings. When the /v parameter is not used, provides only error and warning information. Use the /v switch when errors or warnings are reported in the summary table.
/x: Redirects all output to . This parameter works only with the /test:dns option.
/xsl: or Adds the processing instructions that reference the specified stylesheet. This parameter works only with /test:dnsВ /x: option.
Dcdiag tests
The tables in this section show tests that you can run by using dcdiag. The tests are grouped into the following categories:
Domain controller tests that you cannot skip
Domain controller tests that you can skip
These tests are grouped into two tables based on whether they run by default.
Non-domain controller tests
Domain controller tests that you cannot skip
- Connectivity Checks if domain controllers are registered in DNS, if they can be pinged and if they have LDAP or remote procedure call (RPC) connectivity.
Domain controller tests that you can skip
The following table shows tests that run by default.
Replications Checks for timely replication and any replication errors between domain controllers.
NCSecDesc Checks that the security descriptors on the naming context heads have appropriate permissions for replication.
NetLogons Checks that the appropriate logon privileges exist to allow replication to proceed.
Advertising Checks whether each domain controller advertises itself in the roles that it should be capable of performing. This test fails if the Netlogon Service has stopped or failed to start.
KnowsOfRoleHolders Checks whether the domain controller can contact the servers that hold the five operations master roles (also known as flexible single master operations or FSMO roles).
Intersite Checks for failures that would prevent or temporarily hold up intersite replication and predicts how long it would take for the Knowledge Consistency Checker (KCC) to recover.
Results of this test are often not valid, especially in atypical site or KCC configurations or at the Windows Server 2003 forest functional level.
FSMOCheck Checks that the domain controller can contact a Kerberos Key Distribution Center (KDC), a time server, a preferred time server, a primary domain controller (PDC), and a global catalog server. This test does not test any of the servers for operations master roles.
RidManager Checks whether the relative identifier (RID) master is accessible and if it contains the proper information.
MachineAccount Checks whether the machine account has properly registered and that the services are advertised. Use the /RecreateMachineAccount parameter to attempt a repair if the local machine account is missing. Use the /FixMachineAccount parameter if the machine account flags are incorrect.
Services Checks whether the appropriate domain controller services are running.
OutboundSecureChannels Checks that secure channels exist from all of the domain controllers in the domain to the domains that are specified by the /testdomain parameter. The /nositerestriction parameter prevents dcdiag from limiting the test to the domain controllers in the site.
ObjectsReplicated Checks that the Machine Account and Directory System Agent (DSA) objects have replicated. You can use the **/objectdn:**dn parameter with the **/n:**nc parameter to specify an additional object to check.
frssysvol Checks that the file replication system (FRS) system volume (SYSVOL) is ready.
frsevent Checks to see if there are errors in the file replication system. (Failing replication of the SYSVOL share can cause policy problems.)
kccevent Checks that the KCC is completing without errors.
systemlog Checks that the system is running without errors.
CheckSDRefDom Checks that all application directory partitions have appropriate security descriptor reference domains.
VerifyReplicas Checks that all application directory partitions are fully instantiated on all replica servers.
CrossRefValidation Checks the validity of cross-references.
VerifyReferences Checks that certain system references are intact for the FRS and replication infrastructure.
VerifyEnterpriseReferences Checks that specified system references are intact for the FRS and replication infrastructure across all objects in the enterprise on each domain controller.
/skip: Skips the specified test. You should not specify this parameter in the same command with the /test parameter. The only test that you cannot skip is Connectivity.
The following table shows tests that do not run by default.
Topology Checks that the KCC has generated a fully connected topology for all domain controllers.
CheckSecurityError Reports on the overall health of replication with respect to ActiveВ Directory security in domain controllers running WindowsВ ServerВ 2003 SP1. You can perform this test against one or all domain controllers in an enterprise. When the test finishes, dcdiag presents a summary of the results, along with detailed information for each domain controller tested and the diagnosis of security errors that the test reported.
The following argument is optional:
This argument checks the ability to create a replication link between a real or potential source domain controller (SourceDomainController) and the local domain controller.
CutoffServers Checks for any server that is not receiving replications because its partners are not running.
DNS Includes six optional DNS-related tests, as well as the Connectivity test, which runs by default. You can run the tests individually or together. The tests include the following parameters:
/DnsBasic
Confirms that essential services are running and available, necessary resource records are registered, and domain and root zones are present.
/DnsForwarders
Determines whether recursion is enabled and that any configured forwarders or root hints are functioning.
/DnsDelegation
Confirms that the delegated name server is functioning and checks for broken delegations.
/DnsDymanicUpdate
Checks that the ActiveВ Directory domain zone is configured to do secure dynamic updates and register a test record.
/DnsRecordRegistration
Tests the registration of all essential DC Locator records.
/DnsResolveExtName
Checks the basic resolution of either an intranet or Internet name.
OutboundSecureChannels Checks that secure channels exist from all of the domain controllers in the domain to the domains that are specified by the /testdomain parameter. The /nositerestriction parameter prevents dcdiag from limiting the test to the domain controllers in the site.
VerifyReplicas Checks that all application directory partitions are fully instantiated on all replica servers.
VerifyEnterpriseReferences Checks that specified system references are intact for the FRS and replication infrastructure across all objects in the enterprise on each domain controller.
AD DS displays text, such as naming context names and server names, which contains international or Unicode characters correctly only if you have installed appropriate fonts and language support on the test computer.
Non-domain controller tests
DcPromo Tests the existing DNS infrastructure for any computer that you want to promote to be a domain controller. If the infrastructure is sufficient, you can promote the computer to a domain controller in the domain specified in the parameter **/DnsDomain:**Active_Directory_Domain_DNS_Name. This parameter reports whether any modifications to the existing DNS infrastructure are required. The required argument is **/DnsDomain:**Active_Directory_Domain_DNS_Name.
One of the following arguments is required:
/NewForest
/NewTree
/ChildDomain
/ReplicaDC
If you specify the /NewTree argument, you must also specify the **/ForestRoot:**Forest_Root_Domain_DNS_Name argument.
RegisterInDNS Tests whether this domain controller can register the Domain Controller Locator DNS records. These records must be present in DNS for other computers to locate this domain controller for the Active_Directory_Domain_DNS_Name domain. This parameter reports whether any modifications to the existing DNS infrastructure are required. The required argument is **/DnsDomain:**Active_Directory_Domain_DNS_Name
With the exception of the DcPromo and RegisterInDNS tests, you must promote computers to be domain controllers before you run tests on them.
How to read the output of DNS-enhanced dcdiag
The following steps summarize how to interpret the results provided by DNS-enhanced dcdiag:
Run dcdiag test:DNS /e /f:dns.txt. Microsoft recommends always using the /v switch to obtain verbose information.
Open the report in Notepad or a compatible editor.
Scroll to end of the report and read the summary table.
Identify servers that returned «warn» or «fail» status for any subtest in the summary table.
Review the section of output for that server to see what problem was detected (hint: use the Find command on the Edit menu to search on the string «DC: DC_computername» (without quotes) to locate the detailed section for a given DC.
Resolve problems on DNS clients or DNS server(s) as required.
Run dcdiag /test:DNS /v /e (or /s:DCName) again to verify the fix. Repeat steps 1 through 6 as required until all failures are understood and reconciled.
Warnings and Errors
Dcdiag takes a conservative approach by identifying DNS client or DNS server configurations that may be problematic, do not conform to best practice configurations, or that dcdiag cannot fully validate. Therefore, the summary and detailed sections of dcdiag may report warnings for DNS configurations that are currently functional. Administrators should investigate and validate such configurations when identified by dcdiag.
The tables below contain the configurations that can trigger dcdiag to report warnings or errors for each of the DNS subtests.
Basic
Static IP addresses are recommended for all DNS servers.
DNS server may not be reachable.
Warning: No DNS RPC connectivity (error or non Microsoft DNS server is running)
Disregard this warning if the DNS server is a BIND or other non-Microsoft DNS server.
Warning: The Active Directory zone on this DC/DNS server was not found
Warning: Root zone on this DC/DNS server was found
Error: Authentication failed with specified credentials
DCDIAG requires Enterprise Admin credentials to run all the tests.
Error: No LDAP connectivity
Error: No DS RPC connectivity
Error: No WMI connectivity
DNS test requires WMI connectivity to run on the remote computer.
Error: Can’t read operating system version through WMI
This might be caused by the lack of a WMI connection on the remote computer.
Error: not supported (this tool is supported on WindowsВ 2000, WindowsВ XP, and Windows ServerВ 2003 only)
Error: Open Service Control Manager failed
Unable to find whether the service is running or not.
Error: Kdc/netlogon/DNS/dnscache is not running
Some of the key services are not running.
Error: Can’t read network adapter information through WMI
Error: All DNS servers are invalid
DNS servers that the client is pointing to are either not reachable or not a DNS server, or they have invalid IP addresses.
Error: The A record for this DC was not found
Every domain controller should register a host (A) resource record. Make sure that host (A) records are registered on all the DNS servers that the client is pointing to.
Error: Enumeration of zones failed to find root and AD zone
Error: Could not query DNS zones on this DC
Make sure that the zone in which the domain controller is supposed to register is present.
Forwarder
Error: Forwarders list has invalid forwarder:
Forwarders configured on the DNS server have an invalid IP address or are not a DNS server, or name resolution is not working (that is, cannot resolve forest root domain SRV record if it is a non-root domain domain controller).
Error: Both root hints and forwarders are not configured. Please configure either forwarders or root hints
Make sure that either forwarders or root hints are configured on the DNS server unless it hosts a root zone.
Error: Root hints list has invalid root hint server:
Root hint servers configured on the DNS server have an invalid IP address or are not a DNS server, or name resolution is not working (that is, cannot resolve forest root domain SRV record if it is a non root domain DC).
Configured root hint servers don’t have corresponding IP address. Status field will tell you the status of the server
Error: IP: Status: A record not found
Configured root hint servers don’t have A record.
Error: Enumeration of Root hint servers failed on
Couldn’t list the root hint servers on the target DNS server.
Delegation
Warning: DNS server: IP: Failure: Missing glue A record
The configured delegation is missing glue A record.
DNS server: IP: Error: Broken delegation -verbose
Delegation is configured but the name server is not responding.
DNS server: IP: Error: Broken delegated domain -non-verbose
Error: Failed to enumerate the records at the zone root on the server
DynamicUpdate
Warning: Dynamic update is enabled on the zone but not secure
Secure dynamic updates are recommended.
Warning: Failed to add test record _dcdiag_test_record with error in zone
Test adds a dummy record dynamically
Warning: Failed to delete test record _dcdiag_test_record with error in zone zone
Deletes the added record as well.
Error: Dynamic update is not enabled on the zone
Dynamic update is not enabled on the Active Directory zone so client cannot register its records.
Record registration
Warning: Missing DC SRV record at DNS server
Ignore the error if DNSAvoidRegisterRecord registry key or its Group Policy has been configured to prevent registration of this record.
Warning: Missing GC SRV record at DNS server
Ignore the error if DNSAvoidRegisterRecord registry key or its Group Policy has been configured to prevent registration of this record.
Warning: Missing PDC SRV record at DNS server
Ignore the error if DNSAvoidRegisterRecord registry key or its Group Policy has been configured to prevent registration of this record.
Warning: Record Registrations not found in some network adapters
Error: Missing A record at DNS server :
DC hasn’t registered its A record on the specified DNS server.
Error: Missing CNAME record at DNS server :
DC hasn’t registered its CNAME record on the specified DNS server.
Error: Missing DC SRV record at DNS server :
DC hasn’t registered its DC SRV record on the specified DNS server.
Error: Missing GC SRV record at DNS server :
DC hasn’t registered its GC SRV record on the specified DNS server.
Error: Missing PDC SRV record at DNS server :
DC hasn’t registered specified PDC SRV record on the specified DNS server. All these records can be registered by stopping and starting the netlogon service.
Error: Record registrations cannot be found for all the network adapters
If there are multiple network adapters the test checks whether all the records are present on all the DNS servers configured on each adapter. This error occurs if the record registration is missing on the DNS server.
External name resolution
Error: Internet name cannot be resolved
Specified Internet name cannot be resolved. Make sure the proxy client, servers, root hints, and forwarders are configured properly.
Enterprise DNS infrastructure tests
Warning: Neither forwarders nor root hints are configured from subordinate domain to parent domain
Forwarder or root hints need to be configured in the DNS servers of either the parent or subordinate domains that are hosting the authoritative zones for their respective domain to enable name resolution to work.
Error: Delegation is not configured on the parent domain
Delegation should be configured from parent to subordinate domain.
Error: Delegation is present but the glue record is missing
Delegation is configured but the name servers are missing their glue record.
Error: Forwarders are misconfigured from parent domain to subordinate domain
Forwarders must be configured from subordinate domain to parent domain.
Error: Root hints are misconfigured from parent domain to subordinate domain
Root hints must be configured from subordinate domain to parent domain.
Error: Forwarders are configured from subordinate to parent domain but some of them failed DNS server tests (See DNS servers section for error details)
Forwarders configured have an invalid IP address or are not a valid DNS server, or name resolution is not working (cannot resolve forest root domain SRV record if it is in the non-root domain).
Error: Root hints are configured from subordinate to parent domain but some of them failed DNS server tests (See DNS servers section for error details)
Root hints configured have an invalid IP address or are not a valid DNS server, or name resolution is not working.
Examples
Example 1: A normal domain controller
In this example, you want to examine the domain controller so you can verify that it is healthy and functioning properly. Type the following command at the elevated command prompt:
C:\Windows\system32>dcdiag /s:reskit-DC1 \administrator password
Output similar to the following appears:
Example 2: Failed DNS registration
In this example, you have noticed that one of the domain controllers is not replicating properly. After you verify that the domain controller is operational and can be pinged by IP address, use dcdiag to do an enterprise check. Type the following command at an elevated command prompt:
C:\Windows\system32>dcdiag /s:reskit-DC1 \administrator password /e
Output similar to the following appears:
Example 3: Failed Netlogon Service
In this example, the Netlogon Service has failed on one of the domain controllers. To troubleshoot, type the following command at an elevated command prompt:
C:\Windows\system32>dcdiag /s:reskit-DC1 \administrator password
Output similar to the following appears:
Example 4: Unresponsive or inaccessible server
In this example, you have noticed replication problems. To resolve the issue, type the following command at an elevated command prompt:
C:\Windows\system32>dcdiag /s:reskit-DC1 \administrator password /e