powered by leo blog …
Есть такая интересная штука, как Checkpoint Network SSL и несколько организаций, в которых я тружусь как раз таки ее и использует. Все бы ничего, но из под Linux подключиться к необходимым приложениям решениями из коробки не выходит. Нет, я не хочу сказать, что Checkpoint Network SSL не поддерживает работу с Linux системами, на против, поддержка есть, но установка не так проста…
Как понять, в чем у нас проблема? Да просто, нужно просто запустить браузер и попытаться подключиться по VPN, а далее посмотреть что за ошибка:
Судя по ошибке — возможна проблема с недостающими библиотеками, а проще говоря с зависимостями.. Теперь определим путь программы:
А теперь определим недостающие библиотеки:
Смотрим на 7 и 9 строки того, что вы видите выше, они говорят что в системе недостает модулей libstdc++.so.5 и libpam.so.0, а следовательно нужно установить библиотеки libpam0g и libstdc++5. Ставим:
А это говорит о том, что пакеты стоят. Далее, немного погуглив до меня дошло, что не достает 32 битной версии пакетов, (да и пути установленных модулей как бэ намекают: /lib/i386-…), ну тогда поставим их:
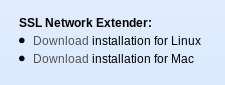
SSL Network Extender
Checkpoint Solutions’ proprietary VPN Firewall solution is called SSL Network Extender. This article documents the manual setup required to properly tunnel into this firewall from a Gentoo Linux host.
To access the VPN from a Linux host, a user logs into a web site using Firefox, then launches a Java applet, which runs a pre-installed local binary (snx) which initiates and configures the tunnel. The setup is elaborate and runs a setuid-root binary, so only attempt this if you trust the firewall server and its administrator, and if you are otherwise confident in the security of the Gentoo host.
Contents
Download the client install script
The client software is only available for download from the firewall appliance itself. The VPN administrator must provide a URL (something like https://vpn.example.com/Login/Login) and credentials.
Log in and click the Settings link.
There is a link to download the software. Click to save the file locally.
Install the client software
There is currently not an ebuild for snx. Run the install script as root.
The script installs /usr/bin/snx and also /usr/bin/snx_uninstall . The main binary is setuid-root, which means that when a non-privileged user runs it, it will run as the root user. Generally this is ill-advised for a system’s security, but it is done here so that a normal user can trigger setting up the tunnel networking.
This binary is also 32-bit and will have linkage errors until the required libraries are installed.
For the three missing linkages it is possible to deduce the packages (with dependencies) that must be installed with 32-bit versions. Configure the necessary changes in package.use.
Now the missing libs can be installed.
and the linkage is fixed
Note that while it is now possible to run snx directly at the command line, it will not result in a successful login. In recent versions it will only work when run as intended, from the browser.
Kernel setup
The snx binary attempts to fork the command modprobe tun and expects a successful exit code. Therefore, CONFIG_TUN must be compiled as a module.
Test that the module loads.
Browser and java plugin
Chrome/Chromium no longer support the NPAPI required to launch java applets, which leaves Firefox as a required browser.
Firefox must launch a java applet. One document on the web stated that Oracle’s JRE is required, and a different document suggested that OpenJDK is acceptable. This document’s author tested using Oracle. Be sure to enable the nsplugin use flag. Before trying to log into the tunnel, run a web search for java test applets and confirm that Firefox is generally successful at launching applets.
Tunnel connection
The system should now be ready to connect to the tunnel. Press the Connect button in the browser.
There will be a variety of trust warnings to click through. The applet will even prompt for your root password and appear to install the binary again. The connection should succeed, however, and subsequent connections will trigger fewer warnings.
getting Checkpoint VPN SSL Network Extender working in the command line
The official Checkpoint out command line tool from CheckPoint, for setting up a SSL Network Extender VPN is not longer working from the Linux command line. It is also no longer actively supported by CheckPoint.
However, there is a promising project, that tries to replicate the Java applet for authentication, that talks with the snx command line utility, called snxconnect .
I was trying to put snxconnect text utility to work in Debian Buster, doing:
However, it was mostly dying either with an HTTP error of:
What to do about it?
PS. The EndPoint Security VPN official client is working well both in a Mac High Sierra and Windows 10 Pro.
2 Answers 2
SNX build 800007075 from 2012, used to support VPN in command line. So I tested it, and lo and behold, it still works with the latest distributions and kernel(s) 4.x/5.x.
So ultimately, my other answer in this thread holds true, if you cannot get hold of SNX build 800007075 or if that specific version of SNX stops working with the current Linux versions (it might happen in a near future) or if you need OTP support.
Presently, the solution is then installing this specific last version of SNX that still supports doing the VPN from the command line.
1) To install snx build 800007075, get it from:
For Debian and Debian-based 64-bit systems like Ubuntu and Linux Mint, you might need to add the 32-bit architecture:
I had to install the following 32-bit packages:
Run then the snx installation script:
You will have now a /usr/bin/snx 32-bit client binary executable. Check if any dynamic libraries are missing with:
You can only proceed to the following points when all the dependencies are satisfied.
You might need to run manually first snx -s CheckpointURLFQDN -u USER , before scripting any automatic use, for the signature VPN be saved at /etc/snx/USER.db .
2) Before using it, you create a
/.snxrc file with the following contents:
3) For connecting, type snx
If you understand the security risks of hard coding a VPN password in a script, you also can use it as:
4) For closing/disconnecting the VPN, while you may stop/kill snx , the better and official way is issuing the command:
see also Linux Checkpoint SNX tool configuration issues for some clarifications about which snx version to use.
5) If automating the login and accepting a new signature (and understanding the security implications), I wrote an expect script, which I called the script snx_login.exp ; not very secure, however you can automate your login, calling it with the password as an argument:
PS. Beware snx does not support OTP alone, you will have to use the snxconnect script present on the other answer if using it.
PPS @gibies called to my attention that using an etoken, the password field gets the password from the etoken and not a fixed password.
When working to install the Firefox official SSL VPN Extender interface in the question VPN SSL Network Extender in Firefox, I found out and solved some more pieces of the puzzle of this question.
Apparently, whilst command line usage of snx from checkpoint has been discontinued, the web based client as described in the linked post still works. However, there is a python command line client, that tries to replicate the Web+Java interface on top of the snx client, and this post is about setting it up to work.
Firstly, the snxvp installed from python pip does not work. There is an updated patched version on https://github.com/agnis-mateuss/snxvpn, that has some useful patches, including an option for ignoring unsigned and/or expired certificates, and more interestingly, being python2 and python3 compatible.
Furthermore, all the URLs on snxconnect.py have to be changed from sslvpn/ to «.
So the step-by-step instructions are roughly:
1) Firstly, installing the snx setup:
If in the VPN, to get the installation file, do:
Otherwise, you will have to get it from the web interface, as described in the linked answer.
For Debian, you might need:
I had to install the following:
You will have now a /usr/bin/snx 32-bit client binary executable. Check if any dynamic libraries are missing with:
You can only proceed to the following points when all the dependencies are satisfied.
Not sure if you need to run first snx -s CheckpointURLFQDN -u USER before using snxconnect , for the signature VPN be saved at /etc/snx/USER.db .
2) Now we have the snxconnect python utility. Such program tries to emulate the web interface, and more interestingly, it does not need Java to authenticate.
So to install and setup snxconnect , run as root:
. then do as root, for python3: (recommended)
. or instead, do as root, for python2:
3) After installing it, you can run as a non-privileged user:
If all went ok, it will ask for the password, and then display:
If you are having problems getting this message, and are instead getting several times in a row, the message: «Unexpected response, try again.», do the Firefox method, and Disconnect and logout properly, waiting a couple of minutes before trying the snxconnect command again.
4) The cookie(s) file will be created at
/.snxcookies, after a successful usage.
After the VPN being established, you can check with ip address or ifconfig you have now a tunsnx interface:
ip route will show you also new routes going through the tunsnx interface.
5) For closing/disconnecting the VPN, while you may stop/kill snxconnect , the better and official way is issuing the command:

