Windows: Как сбросить пароль Windows при помощи Linux
Бывают такие ситуации, когда вы забыли пароль к системе Windows или вам необходимо получить доступ, но вы не знайте пароль учетной записи с правами Администратора. При помощи Fedora Linux, можно быстро и просто сбросить пароль на любой версии Windows. Для этого понадобится сделать загрузочную флешку или записать диск с образом Linux. Записать образ на флешку, можно при помощи утилиты etcher, после чего подключить ее в ПК и следовать действиям описанным ниже. Для описания примера сброса пароля использовался Windows 10 и дистрибутив Linux — Fedora 27.
01. Подключаем загрузочную флешку и перезагружаем ПК.
02. Загружаемся с флешки и выбираем «Start Fedora-Workstation-Live 27» и выбираем «Try Fedora«.
03. Запускаем Terminal.
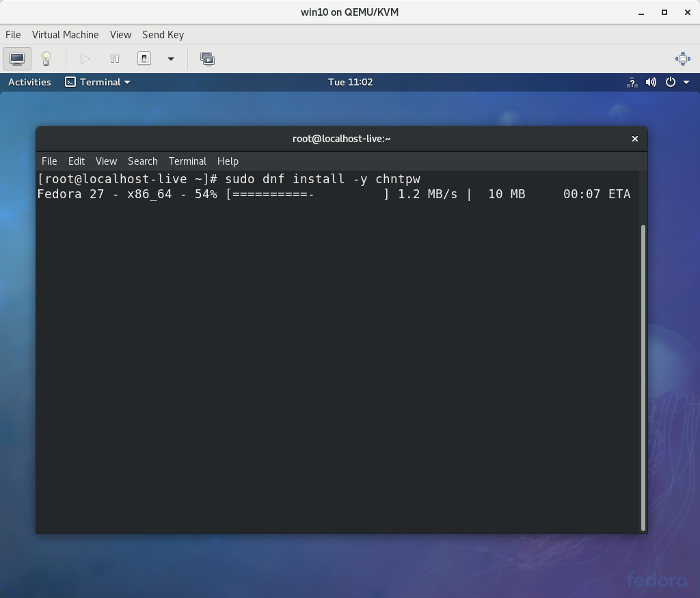
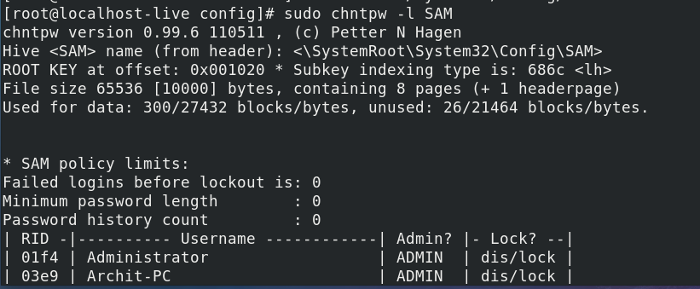
04. Набираем следующие команды для установки chntpw:
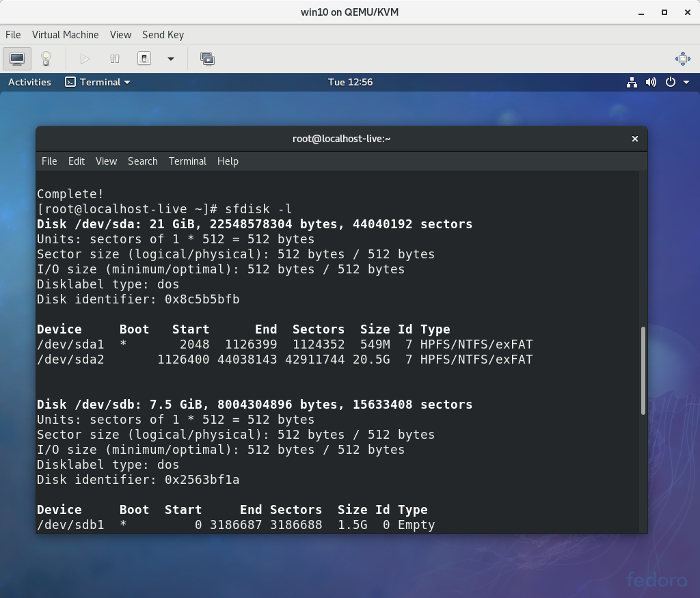
05. Проверяем доступные области жесткого диска:
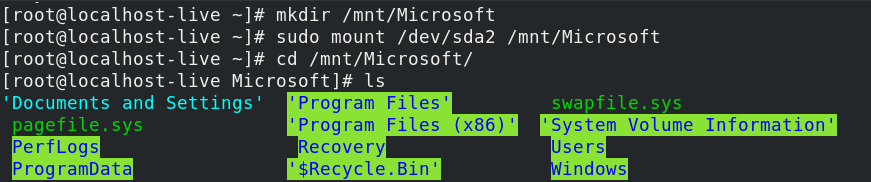
06. Монтируем раздел с Windows (/dev/sda2):
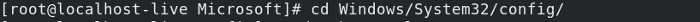
07. Переходим в директорию с SAM записями Windows и запускам chntpw:
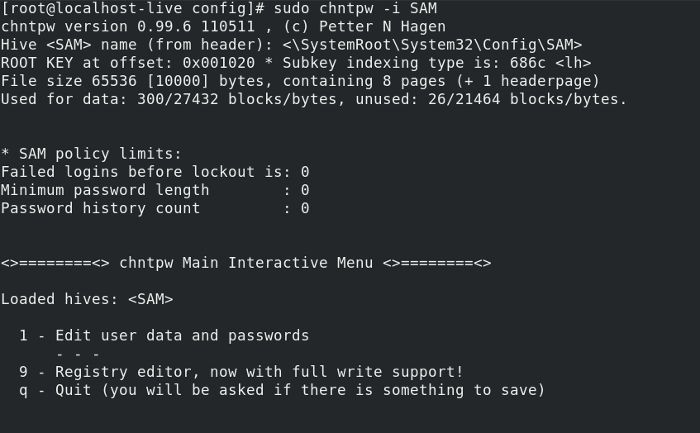
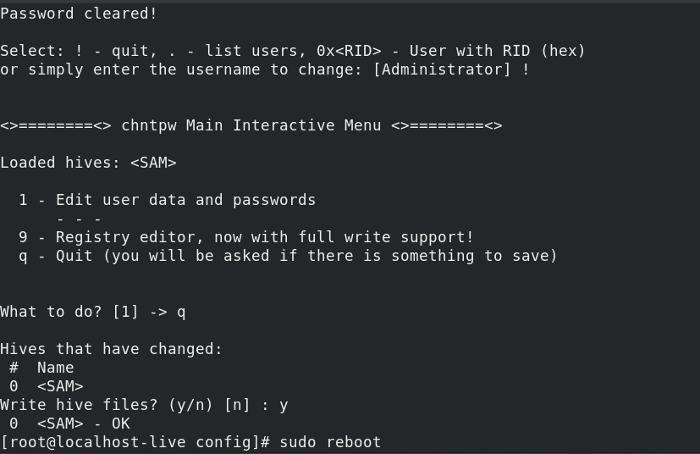
08. Редактируем SAM записи:
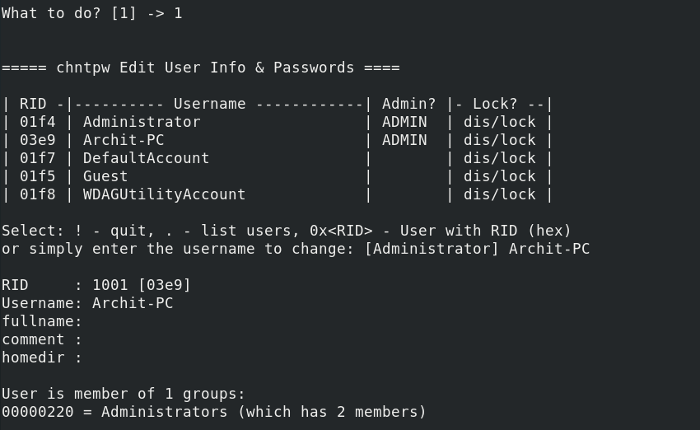
09. Из списка предложных действий выбираем [1]
10. Вводим необходимое имя пользователя из предложенного списка (forbiddenaccess):
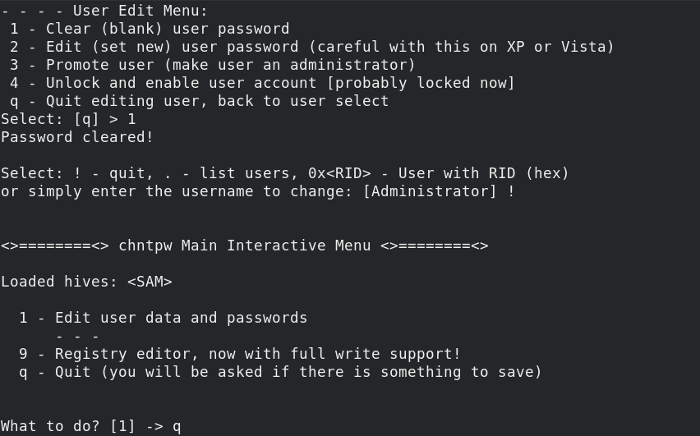
11. Далее выбираем опцию [1] для того, что бы сбросить пароль выбранной учетной записи.
12. Вводим !, затем q и сохраняем изменения в SAM — y
13. Перезагружаем ПК при помощи следующей команды:
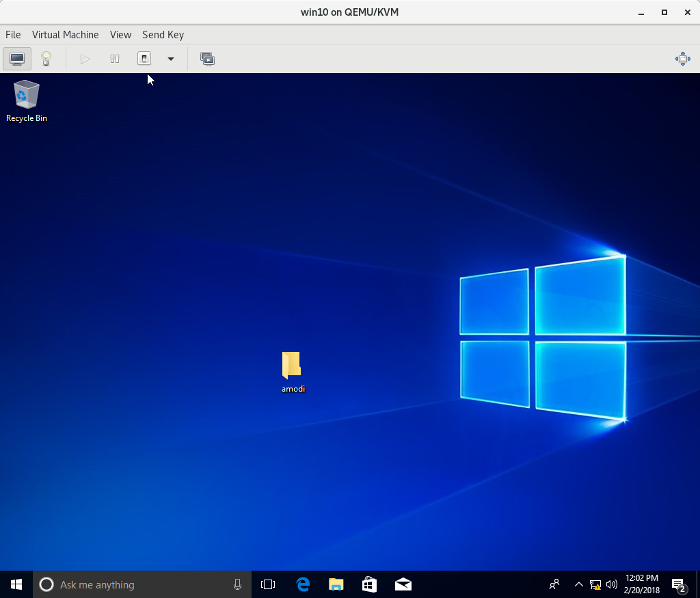
14. Система Windows загружается без запроса ввода пароля
How to reset a Windows password with Linux
Lost your Windows login? The chntpw utility can save the day.
Subscribe now
Get the highlights in your inbox every week.
If you (or someone you know) ever forget your Windows password, you’ll be glad to know about chntpw , a neat Linux utility that you can use to reset a Windows password. For this how-to, I created a Windows virtual machine and set the password to pass123 on my user account, Archit -PC . I also created a Live USB with Fedora 27 using the Fedora Media Writer application.
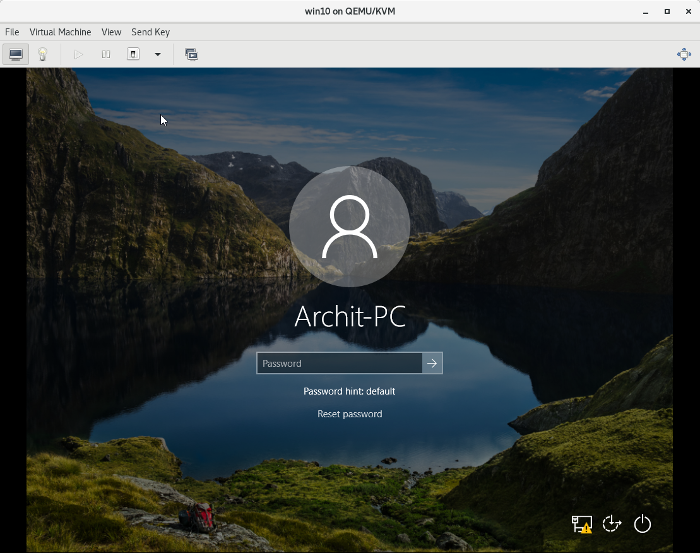
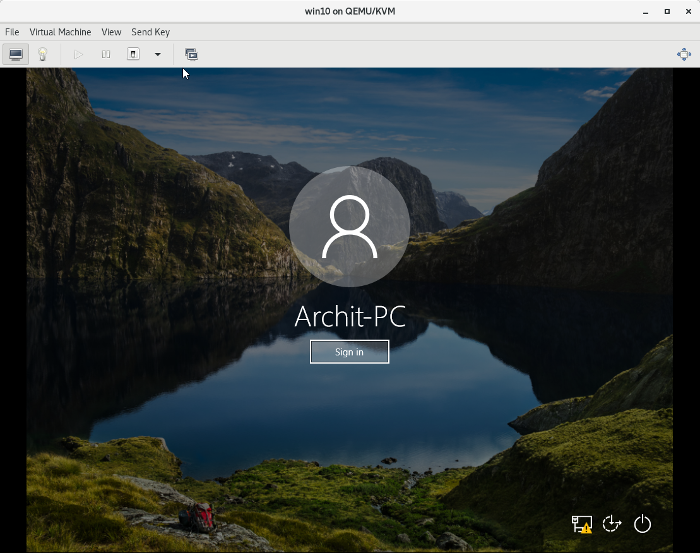
1. Attach the Live USB to your PC and restart from the login screen, as shown below:
passwordreset_login-pass.png
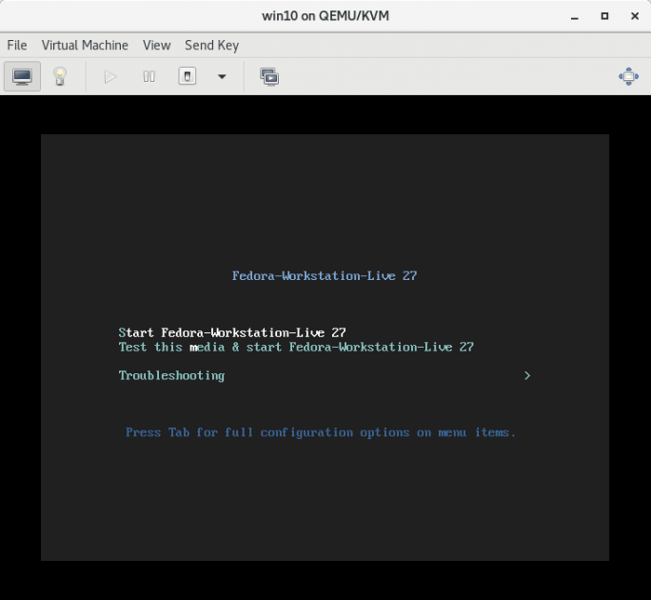
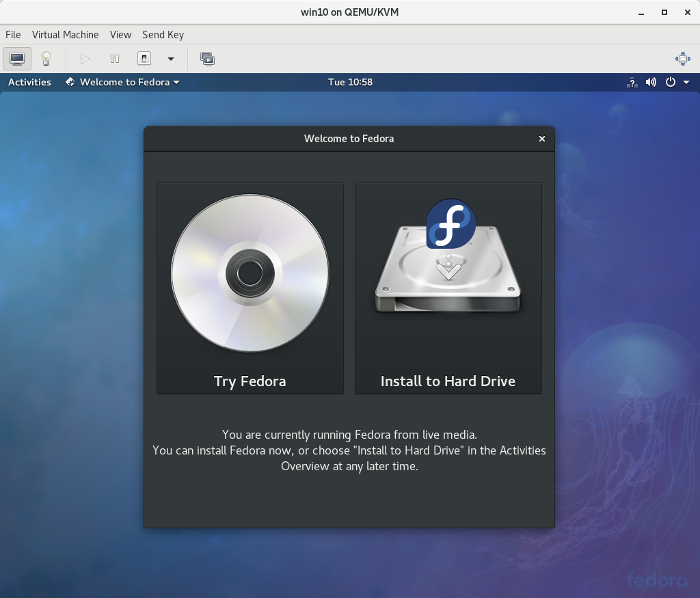
2. Boot from the Live USB and click on Try Fedora:
passwordreset_boot.png
passwordreset_try-fedora.png
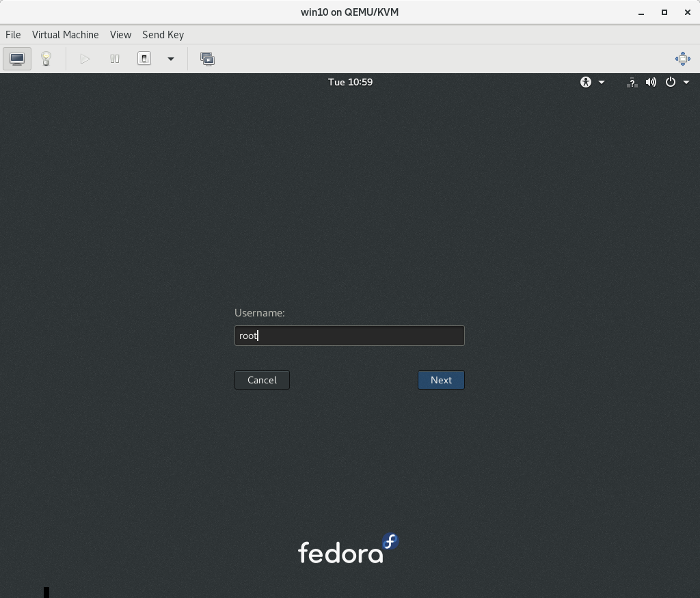
3. Log out from live-user and log into root . This step is not necessary, but I prefer to use the root user to bypass any permission issues:
passwordreset_root.png
4. Install the chntpw utility with the following command (you’ll need a live internet connection for this):
passwordreset_install.png
5. Check which partition should be mounted by sfdisk -l .
passwordreset_sfdisk.png
and mount that partition (e.g., /dev/sda2 ) with the following command:
mount-1.png
Change the current directory to the config directory:
passwordreset_mount-2.png
Also, check the user records in the Security Account Manager (SAM) database:
passwordreset_mount-3.png
6. Edit the SAM database with the command:
Then type 1 (for Edit user data and passwords ):
passwordreset_username-1.png
And type your user account name (i.e., Archit-PC in this example) for the username:
passwordreset_username-2.png
7. Type 1 to clear the user password or 2 to set a new password for the Archit-PC user, then quit and save the changes:
passwordreset_clear-1.png
passwordreset_clear-2.png
8. Reboot to Windows. If you selected 1 above, you’ll see there’s no password required to log in. Just click Sign in and you will be logged in:
passwordreset_nopass-1.png
passwordreset_nopass-2.png
That’s all there is to it! I hope this will be helpful if you ever need to reset a Windows password.
Topics
About the author
Recommended reading
30 Comments
Spotted a small glitch. Looks like the screenshot that supposed to illustrate the execution of a mounting command, sudo mount /dev/sda2 /mnt/Microsoft/, is wrong. For me it shows the result of the execution of a chntpw command, sudo chntpw -i SAM.
Oh that’s correct, thanks for finding it!! 🙂
Archit, If you send over a revised screenshot, I can swap it out.
Thanks a lot Rikki, i’ve sent the revision 🙂
While I love Fedora clonezillia has chntpw already there.
I have clonezilla on my pxe boot arsenal.
Great, I got to give it a try!
This is great! Thanks for sharing. I have used Linux to rescue a number of crashed/trashed Windows computers. This is the most complete description I have ever seen of how to use chntpw.
Superb beginning of the day 🙂 thanks for this post :+1
«3. Log out from live-user and log into root. This step is not necessary, but I prefer to use the root user to bypass any permission issues:
passwordreset_root.png
Logging in as root
4. Install the chntpw utility with the following command (you’ll need a live internet connection for this):
sudo dnf install -y chntpw»
You are saying log in as root. You don’t need sudo if you are already root.
Thanks John, that’s correct. I used this command so that a person using live-user can also execute it without any modifications, hope this makes sense. 🙂
Thanks for sharing! I have used chntpw for years. This utility can also run from Ubuntu Live CD.
There are also other free alternatives that can break a lost windows password. For instance, using Ophcrack or a Windows install disk:
http://ophcrack.sourceforge.net/
https://www.top-password.com/blog/reset-windows-10-password-with-sticky-.
Oh cool, thanks for sharing, will definitely try these out! 🙂
Thanks for the tip, might come handy! BTW you don’t need to use sudo if you’re already working as root.
Wow! Didn’t know about this. Nice article!
Thanks for the great tutorial. More grease to your elbows.
This only works if your Windows drive is not encrypted. If you have encrypted it using the storage option of Windows, you won’t even be able to mount the volume correctly and edit its content from an external tool to clear the password stored in the SAM registry file, you first need the password.
It may also not work if the encryption password comes from the TPE module which won’t allow you to boot from the external drive which was not first allowed to run as it was not signed.
But anyway it’s good to signal users that their Windwos password is not a real protection for their data, and that it can be easily cleared in most cases: suppose your PC is stolen (or seized by the police/justice. ), they know what they can do easily to enter your drive and get access to all the contents.
Also clearing a password this way may invalidate all access tokens that allow you to use some remote sites or storage that will need a new authorization, because the SAM database will no longer have the necessary access tokens.Your PC will then be «disconnected» from a secure corporate domain and you’ll need to contact the domain admin to reauthorize your PC (and fbefore they accept to reconnect you they’ll want to inspect your PC, and may force you to resintall it completely).
So don’t do that to bypass the protections that have been set in a corporate domain against such personal use of a PC you don’t really own and have no right to adminsiter yourself.
Wow, thanks for the very useful info!! Totally agree about the disk encryption and thanks for sharing about TPE, didnt know it! :))
I thought we can just rename cmd to sethc and press ctrl alt del when reboot windows.
I havent tried this yet, but the article specifies how to reset it with Linux, so keeping the scope limited to Linux 🙂
Why using sudo, when you are with root?
nice review, and very crystal clear steps! Great JOB!
I guess i was looking to provide universal steps irrespective of user, so sudo would be useful for non-root users. Thanks :))